Got to know JMI official website is being defaced by some unidentified hacker (or I say Romeo :p), here are few things that Jamia’s website administrator and information security personnel would like to do, to get the website back.
Read: Jamia Millia Islamia Website Hacked; Hacker Wishes Happy Birthday to Pooja
Things to check by website administrator to recover defaced JMI webpage.
A website administrator can look up into the directories where files related to the jmi.ac.in website is kept. He may check for any file which looks alien to him.
In most of the cases, hacker put the malicious file in the root directory with spunky names – like h@ck3d, @noNymou5 etc. If an administrator finds such file, he can choose to replace it with the original (backed up) file of the website.
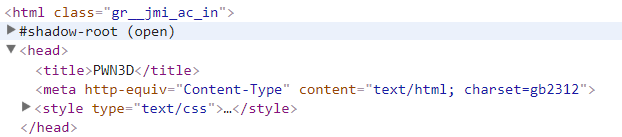
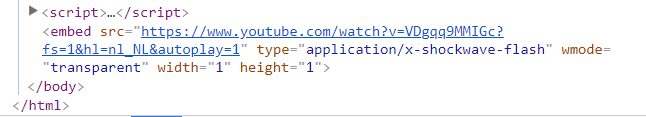
Once the website is back to normal the administrator can look for any un-identical or unidentified user and remove the same once found. Hacker most of the time create user ID to maintain the access to the website and create the backdoor.
Things to do for information security administrator
An information security administrator here has a greater task to identify who is the person behind this cyber attack. Jamia being a reputed university of India, may need to prosecute the person so that such activity does not happen again in the future.
The information security person first needs to identify which IP used to deface the website. In order to get the IP detail, he may need to correlate the events of Firewall, Intrusion Detection System and the server where JMI website is hosted.
In a real environment, it is very common for a hacker to use a proxy in order to hide his original IP. But still, a cybersecurity personal can get the original IP if he looks into the X-Forwarder IP in the intrusion detection logs.
Once the information security person has the IP address he can utilize many open source tools to get the ISP and location of the IP address.
Jamia, in that case, may contact the ISP asking the full address of the machine using the particular IP.
These are few things a website administrator and information security person may do. Yeah, there are many other things to do.. the sky is the limit.
(Written By Rehan Alam, He is a Jamia Alumnus and working in US based MNC as Information Security Consultant and also a blogger at CybrNow.com)
